
***********************************************************************************
* Description: Renewal HTTPS SSL Certificate for Oracle WebLogic Fusion Middleware
* Date: 11:42 PM EST, 03/01/2018
***********************************************************************************
<1> For security purpose, majority orgnization utilize HTTPS SSL\TLS to encrypt data for online transaction.
|
|__ o. To archive the goal, third party issue digital cerificate is needed.
|
|__ o. Generally, cerificate validation date is not perminent, and needs renewal 2 or 3 yearly basis.
|
|__ o. To receive the new certificate, you need to submit your Certificate Signing Request [CSR] to your Certificate Authority.
|
|__ o. For WebLogic HTTP server, you need to create an Oracle wallet, and put all the Trusted cerificate and regular certificate within it to make it valid.
|
|__ o. If the old certificate going to expire, basiscally, you need to delete the old one, importing new one, and restart OHS.
|
|__ o. The cerificates has 2 types, Trusted Certificate and Regular Certificate.
|
|__ o. The purpose of Trusted Certificate is for "OK, I know and this GoDaddy as my CA. So, I have no doubt on all the certs issued from it."
| Usually, if you still use same CA for the renewal, you do not need to re-import Trusted Certificate again.
|
|__ o. Regular cerificate is for app user visting your website via HTTPS protocal, which needs to be re-import as renewal.
|
|__ o. CAUTION: What we trust is the vendor or CA who issues the cerificate, not the cerificate itself.
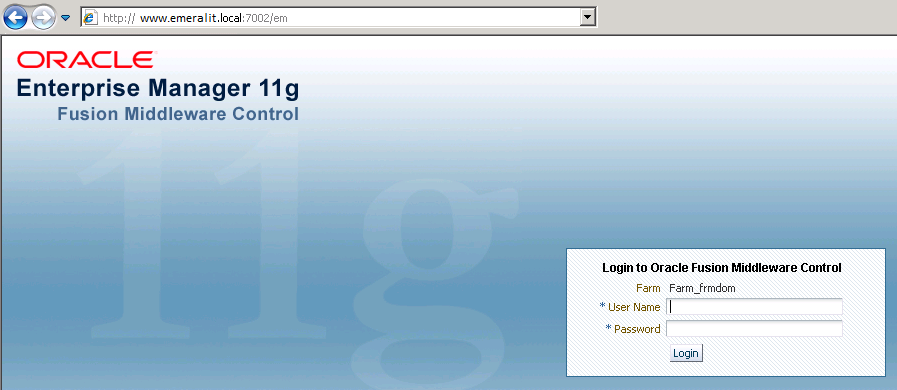
<2> Step 1 - Submit "Certificate Signing Request" through Fusion Middleware dashboard for WebLogic HTTP server:
|
|__ o. The default port is 7002, which needs to be indicated appending to console URL:
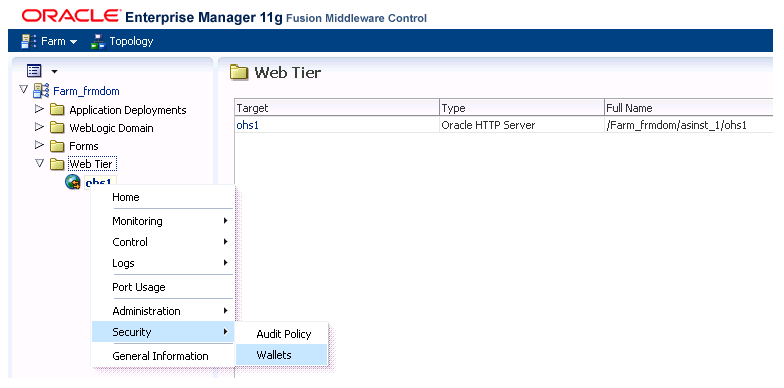
 <3> Step 2 - After log into the console, finding existing wallet first. Go to "Web Tier" ==> Right click on "ohs1" ==> "Security" ==> "Wallets":
<3> Step 2 - After log into the console, finding existing wallet first. Go to "Web Tier" ==> Right click on "ohs1" ==> "Security" ==> "Wallets":
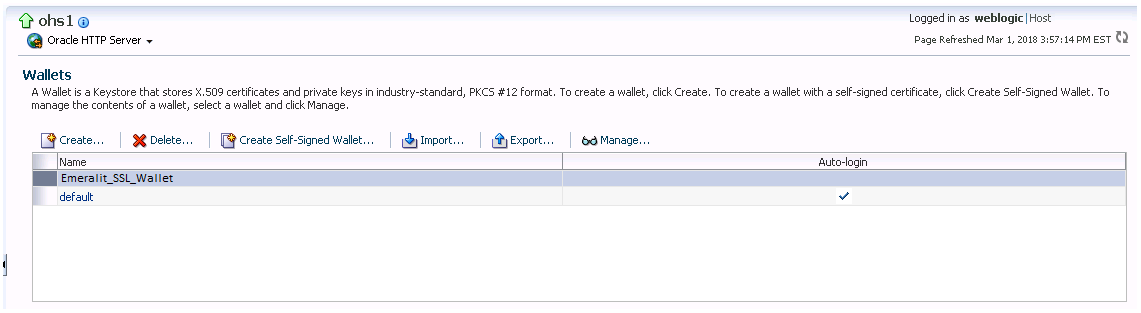
 <4> Step 3 - Each wallet is corresponding to a physical folder on the server. For this case, the wallet location is below:
|
|__ o. Default wallet ............. /Data/Oracle/Middlewarenew/asinst_1/config/OHS/ohs1/keystores/default
| User created wallet ........ /Data/Oracle/Middlewarenew/asinst_1/config/OHS/ohs1/keystores/emeralit_SSL_wallet
|
|
|__ o. Before importing the new cerificate, Click on "Export" button, or copy the physical folder as a backup method.
|
|
|__ o. "Auto-login" means no password is needed.
<4> Step 3 - Each wallet is corresponding to a physical folder on the server. For this case, the wallet location is below:
|
|__ o. Default wallet ............. /Data/Oracle/Middlewarenew/asinst_1/config/OHS/ohs1/keystores/default
| User created wallet ........ /Data/Oracle/Middlewarenew/asinst_1/config/OHS/ohs1/keystores/emeralit_SSL_wallet
|
|
|__ o. Before importing the new cerificate, Click on "Export" button, or copy the physical folder as a backup method.
|
|
|__ o. "Auto-login" means no password is needed.
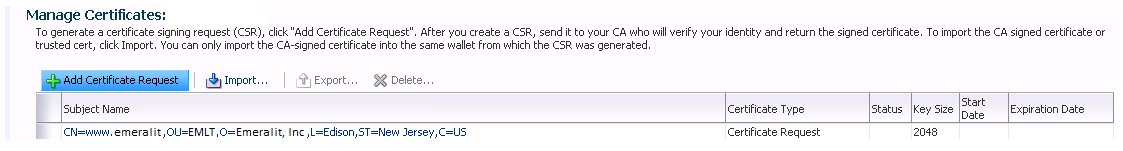
 <5> Step 4 - Submitting Certificate Request:
<5> Step 4 - Submitting Certificate Request:
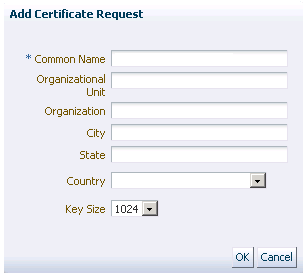
 <6> Step 5 - Fulfill the Company or Orgnization Information:
<6> Step 5 - Fulfill the Company or Orgnization Information:
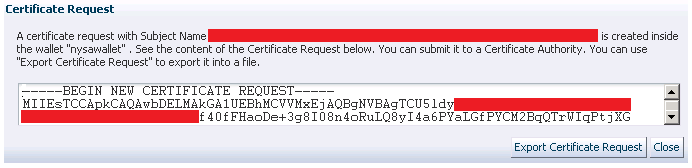
 <7> Step 6 - Export and send over the encrypted request to your Certificate Authority:
<7> Step 6 - Export and send over the encrypted request to your Certificate Authority:
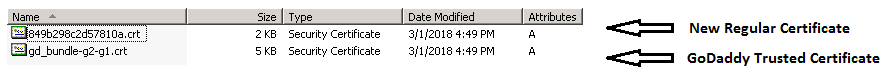
 <8> Step 7 - After CA approves your CSR, a zipped package including Trusted Certificate and Regular Certificate will be sent over:
<8> Step 7 - After CA approves your CSR, a zipped package including Trusted Certificate and Regular Certificate will be sent over:
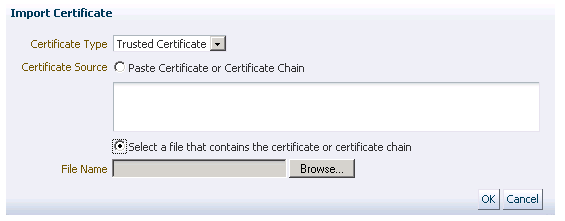
 <9> Step 8 - After zipping the package, you can pick up the option for paste or upload to import the certificate accordingly:
|
|__ o. In this case, user still use GoDaddy as vendor, so aftering deleting the old regular cerificate, you can import the new one.
<9> Step 8 - After zipping the package, you can pick up the option for paste or upload to import the certificate accordingly:
|
|__ o. In this case, user still use GoDaddy as vendor, so aftering deleting the old regular cerificate, you can import the new one.
 <10> Step 9 - To make the new certificate being actived, OHS needs to be restarted once:
|
|__ o. Right click on "ohs1" ==> "Control" ==> "Restart"
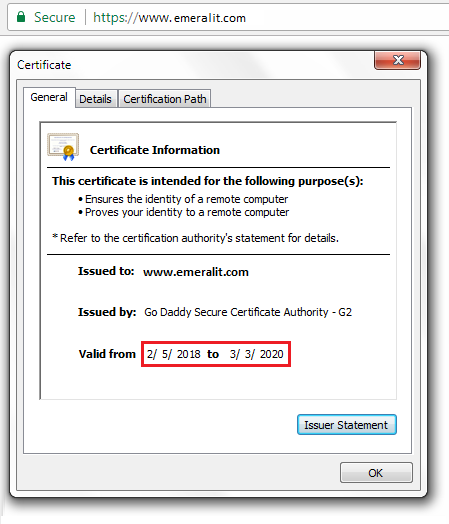
<11> Step 10 - Go to website, and click on the "LOCK" icon next to website address to verify new cerificate is being used:
<10> Step 9 - To make the new certificate being actived, OHS needs to be restarted once:
|
|__ o. Right click on "ohs1" ==> "Control" ==> "Restart"
<11> Step 10 - Go to website, and click on the "LOCK" icon next to website address to verify new cerificate is being used:
Your Comments