
********************************************************************************
* Description: Send command from MSWIN AWS CLI to Linux server on cloud via SSM
* Date: 12:09 PM EST, 03/19/2018
********************************************************************************
<1> In some practical cases, a large company's IT environment could contain hundred or thousand servers on AWS Cloud needs to be patched:
|
|__ o. AWS provides an option that SYS admin can send Linux command within an API request to remote servers from Windows latop to remote servers, performing operation in batch.
<2> Step 1 - Download and install AWS CLI for Windows platform:
|
|__ The Windows 64-bits .msi installer attached as "Download" option with the itme.
|
|__ Reference: https://docs.aws.amazon.com/cli/latest/userguide/awscli-install-windows.html#awscli-install-windows-path
<3> Step 2 - Create AWS programatic access key pair:
|
|__ o. Login AWS Console
==> AMI
==> Users
==> Click on the choosen "username"
==> Security Credentials
==> Create access key
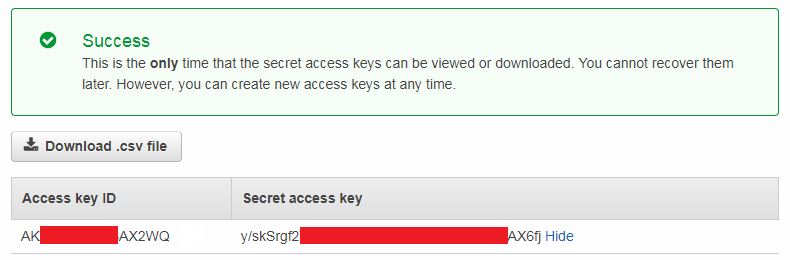
==> Save "Access key ID" [like username] and "Secret access key" [similar to password].
CAUTION: "Secert access key" only show up once when it got created. So, it needs to be saved properly somewhere.
 <4> Step 3 - Configuring AWS CLI with "Access Key Pair" on local Windows laptop via CMD:
|
|__ CMD> aws configure
AWS Access Key ID: AKIOK8RM2WTOJ8J2HWSQ
AWS Secret Access Key: BYpos8lDuuKPpqmJdqIdOl2UYZglXfydKhlLwqI+
Default region name [us-east-1]: us-east-1
Default output format [json]: json
<5> Step 4 - Install Amazon Service System Manager[SSM Agent] on remote Cloud Linux servers:
|
|__ o. SSM is acting as an agent receiving commands from remote servers via AWS API to munipulate AWS services without log into console.
|
|__ o. Reference - https://docs.aws.amazon.com/systems-manager/latest/userguide/ssm-agent.html
|
|__ o. Different Linux Platform and version have various installation utility or method:
|
|
|__ a) Redhat [64-bit]:
|
|
| $ yum install -y https://s3.amazonaws.com/ec2-downloads-windows/SSMAgent/latest/linux_amd64/amazon-ssm-agent.rpm
| $ systemctl status amazon-ssm-agent ............ [RHEL 7.x]
| $ status amazon-ssm-agent ...................... [RHEL 6.x]
|
|
|__ b) Ubuntu [64-bit, either of below installation utility]:
$ wget https://s3.amazonaws.com/ec2-downloads-windows/SSMAgent/latest/debian_amd64/amazon-ssm-agent.deb
$ dpkg -i amazon-ssm-agent.deb
$ status amazon-ssm-agent ..................... [Ubuntu 14.x]
$ systemctl status amazon-ssm-agent ........... [Ubuntu 16.x]
<6> Step 5 - Grant SSM Policy to either AWS user or EC2 server IAM role:
|
|__ o. IAM Role:
| |
| |__ o. Login AWS console, and go to "IAM"
| | ==> "Roles"
| | ==> "Create Roles"
| | ==> "AWS Services"
| | ==> "EC2"
| | ==> "EC2 Role for Simple Systems Manager"
| | ==> "AmazonEC2RoleforSSM"
| | ==> Assign the role to target EC2 instance.
| |
| |__ o. CAUTION: One EC2 instance could have only one IAM role, but "AmazonEC2RoleforSSM" can be attached with existing role.
|
|
|__ o. AWS user:
|
|__ o. If the user have "Administor" permission, you can "add permission" and "attach existing policy directly" with "AmazonSSMFullAccess".
<4> Step 3 - Configuring AWS CLI with "Access Key Pair" on local Windows laptop via CMD:
|
|__ CMD> aws configure
AWS Access Key ID: AKIOK8RM2WTOJ8J2HWSQ
AWS Secret Access Key: BYpos8lDuuKPpqmJdqIdOl2UYZglXfydKhlLwqI+
Default region name [us-east-1]: us-east-1
Default output format [json]: json
<5> Step 4 - Install Amazon Service System Manager[SSM Agent] on remote Cloud Linux servers:
|
|__ o. SSM is acting as an agent receiving commands from remote servers via AWS API to munipulate AWS services without log into console.
|
|__ o. Reference - https://docs.aws.amazon.com/systems-manager/latest/userguide/ssm-agent.html
|
|__ o. Different Linux Platform and version have various installation utility or method:
|
|
|__ a) Redhat [64-bit]:
|
|
| $ yum install -y https://s3.amazonaws.com/ec2-downloads-windows/SSMAgent/latest/linux_amd64/amazon-ssm-agent.rpm
| $ systemctl status amazon-ssm-agent ............ [RHEL 7.x]
| $ status amazon-ssm-agent ...................... [RHEL 6.x]
|
|
|__ b) Ubuntu [64-bit, either of below installation utility]:
$ wget https://s3.amazonaws.com/ec2-downloads-windows/SSMAgent/latest/debian_amd64/amazon-ssm-agent.deb
$ dpkg -i amazon-ssm-agent.deb
$ status amazon-ssm-agent ..................... [Ubuntu 14.x]
$ systemctl status amazon-ssm-agent ........... [Ubuntu 16.x]
<6> Step 5 - Grant SSM Policy to either AWS user or EC2 server IAM role:
|
|__ o. IAM Role:
| |
| |__ o. Login AWS console, and go to "IAM"
| | ==> "Roles"
| | ==> "Create Roles"
| | ==> "AWS Services"
| | ==> "EC2"
| | ==> "EC2 Role for Simple Systems Manager"
| | ==> "AmazonEC2RoleforSSM"
| | ==> Assign the role to target EC2 instance.
| |
| |__ o. CAUTION: One EC2 instance could have only one IAM role, but "AmazonEC2RoleforSSM" can be attached with existing role.
|
|
|__ o. AWS user:
|
|__ o. If the user have "Administor" permission, you can "add permission" and "attach existing policy directly" with "AmazonSSMFullAccess".
Your Comments